
First, let’s be really clear and understand that codes, ciphers, and anything intended to “disguise the meaning” of a message is strictly against FCC rules on all radio services usable by the public. This includes Citizens Band (CB), Amateur Radio, Family Radio Service (FRS), and General Mobile Radio Service (GMRS).
That being said, when the SHTF you may need the ability to convey information to your group, contact like-minded groups, or identify friendlies approaching the area. This will need to be done in a manner that doesn’t compromise your group, location, or the information.
Like any other aspect of preparedness, you need to plan this BEFORE something happens. This is something you will need to practice. You can practice in a number of different ways without making transmissions over the air. Send the encrypted message in an email or by other electronic means or even use a dead drop.
Communications Security (COMSEC)

COMSEC is the art of keeping communications from being intercepted in a usable form. This includes physical security of equipment, code books, and encryption keys. Only those with a strict need to know should have access to communications items. This is especially the case with techniques used to code messages, authentication methods, code words etc. The medium and methods used to share them between friendly groups is also part of COMSEC. If you want to have the highest level of protection for your codes and ciphers they should never be sent by electronic means, i.e., email. The next best compromise is to use a trusted encrypted email, but in this day and age do we really know if something is secure? The best practice is to hand them directly to the intended recipient. The methods used to create the codes and ciphers should avoid a computer, or at least use one that has never been connected to the internet.
Codes and ciphers are typically broken because of repetition, so it’s important not to use a code or cipher more than once if possible. The more it’s used the greater the risk of it being broken.
There are several different methods and types of codes and ciphers. Each have their uses and limitations:
Voice Encryption
Modern voice encryption uses Advanced Encryption Standard (AES). It was approved in 2001 and now mandated for use by all Federal agencies. AES replaced Data Encryption Standard (DES) that was used before. Even though AES in the accepted standard there are still many local law enforcement agencies who either don’t use any encryption or still use the DES standard due to the costs associated with upgrading. More and more local law enforcement agencies are implementing encryption on their radio systems when they upgrade to P25 systems.
A device called a key loader is needed to generate the encryption keys and to put them into the radios. Radio equipment with DES encryption can be found on a popular bidding site for around $400 with a corresponding key loader for about $400. AES standard radios can be found for between $800 – $1,000 with compatible key loaders around $1,000 – $2,000. Obviously, these costs are outside the budget of most of us.
Without knowing the encryption key it’s almost impossible to decrypt the transmission if AES is being used. If DES encryption is used it’s possible to break it with modern computers. As with other basic COMSEC procedures regularly changing the encryption key reduces the chance that communications can be compromised. However, because of the logistics required to coordinate changing encryption keys in a fleet of radios, poor COMSEC procedures often compromise the encryption.
There are some ham radios on the market that have a ‘scramble’ function. This is usually simple voice inversion. Because there isn’t a unique ‘key’ and it’s available in all radios from the same manufacturer it’s not considered a violation of FCC rules.
“The question you ask has been asked before. Section 97.113 prohibits amateur stations from transmitting messages in codes and ciphers intended to obscure the meaning of the message. If the code or cipher is publicly available, then transmitting messages in the code or cipher would not appear to be for the intent of obscuring the meaning of the message.
William Cross FCC”
Message Authentication
Message authentication is a process to validate that the sender of the message is who you think they are or who they claim to be. Obviously, this is easier if you recognize the voice of the operator. However, you also need a method that could be used by the sender to indicate they are sending under duress. During World War II spies were paired with a specific receiving operator during training so the receiving operator could recognize the ‘flow and rhythm’ of the sender as part of COMSEC.
One method of authentication is to use a simple word challenge with a corresponding response. These are commonly used at sentry posts where anyone approaching must respond with a word or phrase when challenged. The challenge and response words should not have an association, i.e., the normal automatic response to “bread” would be “butter.” So, you should have something like “bread” and “carrots.” Challenge words are not efficient for over the air use because once used it’s compromised if anyone is listening.
To be used over the air a longer list is needed. It can be a word that is added at the beginning or end of a transmission based on a rotation. It can be a matrix with the day and date on a table which gives the word to be used. Alternatively, it can be a challenge/response where the receiver issues a challenge from a list and the other person must respond with the corresponding response. An example is the isogram or DRYAD sheet discussed below. No matter what the method, the code word or phrase should only be used once.
A more subtle authentication uses a phrase that could possibly be part of a normal conversation or message that both parties know is an authentication. There should always be a word or phrase that is used to indicate that the sender is sending under duress but would appear to be an approved authentication.
ISOGRAMS
An isogram is a word or phrase without a repeating letter. To use in message authentication, you need a word that is at least 10 letters long. Each letter is assigned a sequential number.
| A | F | T | E | R | S | H | O | C | K |
| 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 |
A challenge would be: “Authenticate Echo”
The response would be: “I authenticate four”
The more times the authentication is used the more information an adversary can obtain and figure out the word, rather like the game hangman. Obviously, the whole word should never be said over the air. As with all cryptology the more frequently a code is changed the less chance there is that someone will figure it out. This is called the crypto-period. Use random letters rather than words from a dictionary because of computerized programs designed to decrypt a message. The drawback is that a word is easier to remember whereas random letters would need to be written down.
CODE WORDS
Code words are used to identify people, units, locations, actions, and many other uses. There should be no association between the code word and whatever it refers to.
They should be changed regularly, such as for each mission or daily. A master list should be created and then each word crossed off when used so there’s no risk that it’s used again. The only people who have access to the entire list of words are those responsible for assigning them to something. A good way to generate words is to search lists for names, planets, ships, etc. used in TV shows and movies, especially science fiction shows or movies. Using lists like this reduces the possibility of using a word that might be needed in a normal message.
Obviously, COMSEC needs to be strictly followed so ensure that the list of words being used for the specific mission isn’t compromised.
DRYAD SHEET
A DRYAD sheet was developed by the U.S. Army and was in use until modern encryption became available. Part of a DRYAD sheet is shown below. The alphabet is shown in the left column, across the top are numbers and letters, and in the boxes, are random letters.
The start and end date time group (DTG) are the crypto period, the period during which this sheet is valid. The UID is unique ID, so that you know which sheet to use.
To use the DRYAD sheet for authentication the requestor selects a letter from the left most column and then a random letter in the corresponding row. The person being challenged will find the corresponding letter on their copy and respond with the letter below, or some other agreed pattern, such as the 2nd one below. For example; “Authenticate bravo victor.” The response would be; “I authenticate whiskey.” Or the agreed response could be the one below and the one to the right. In that case the response to “bravo victor” would be “whiskey delta”. Once a combination has been used it’s crossed off so that it’s not used again.
Using a DRYAD for message encryption is beyond this article. For more examples of DRYAD sheets and their use I highly recommend Signals Handbook for Small Teams. The author also has a couple of programs to generate DRYAD sheets. As with all code generators the longer the key used to generate the encryption the more secure it is. Mashing the keyboard until the program won’t take any more characters is one way of generating a key that could probably never be repeated. Never use a computer clock as the key as this is predictable.
| For Official Use Only | UID: | |||||||||
| Start DT G: | End DTG: | |||||||||
| Distribution: | ||||||||||
| ABCD | EFG | HIJ | KL | MN | OPQ | RS | T UV | WX | YZ | |
| 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | |
| A | OLCW | QXF | TAN | DJ | GE | SIV | BY | UZM | HP | KR |
| B | GMSP | VDJ | HRL | EU | OC | WYT | FQ | ZNI | BX | AK |
| C | AULV | WYN | MIG | KQ | XJ | CZB | ES | OHF | PT | RD |
| D | YFCQ | PAG | ESJ | KL | ZW | RBO | MV | IHT | XD | NU |
| E | CLNE | WQS | DIV | FM | YK | JPA | GB | XUT | HO | RZ |
| F | HOYU | TGX | QNS | BW | IM | KCE | RV | DAL | PZ | FJ |
CODEBOOK
A codebook shouldn’t be considered encryption but rather a way to convert longer words to a shorter representation, such as three or four numbers or letters. One code should be for “do not answer”. Care should be taken to avoid repeating a number or letter combination when creating a codebook. In The Complete Guide To Secure Communications With The One Time Pad Cipher by Dirk Rijmenants, the author provides blank codebooks with error correction. The numbers differ from all others by at least two digits and there is no transposition of neighboring digits. This prevents errors when sending the message. A 3-digit codebook will give you 100 words or phrases, a 4-digit codebook will give you 807 words or phrases.
The Dirk Rijmenants has a large number of articles on encryption, also check the articles under ‘papers’ on his web page.
BOOK CODE
There are a number of techniques to encode a message without the use of modern equipment, such as a computer or sophisticated encryption programs. Several of these techniques were used during World War II with great success. Probably one of the most widely known is a book code. However, these can be broken easily with modern computers as the entire library of all books and all their editions are stored electronically. Because of this I would not recommend using a book code.
ONE-TIME PAD CIPHER
One-time pad (OTP) uses a plaintext of random letters or numbers. This is then paired with the text to be sent. The resulting encrypted message with apparently random letters or numbers is then sent. The receiver reverses the process to decrypt the message. “Pad” comes from the original use where a small note pad contained the random letters. The page of the pad is used once and then destroyed. Spies usually have the pads printed on paper that is digestible or on flash paper which is something magicians use.
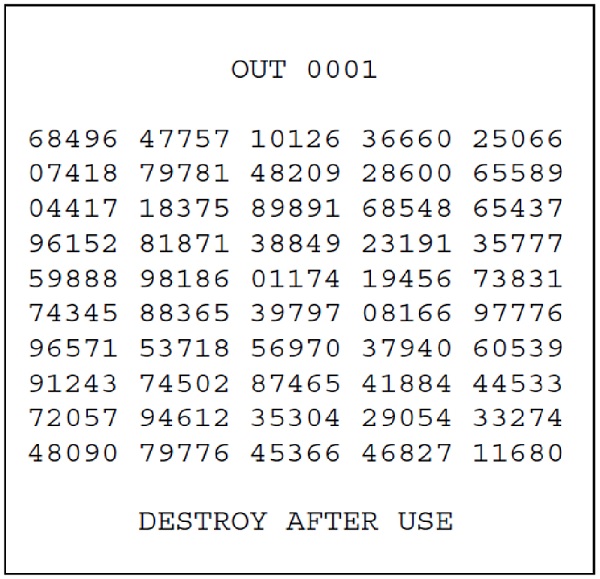
Typical OTP: the first set of 5 numbers represent the specific OTP, source: The Complete Guide to Secure Communications with the One Time Pad Cipher by Dirk Rijmenants
Versions of a one-time pad cipher that use numbers are more versatile. A “check board” is used containing numbers, letters, and characters such as spaces and periods that are then converted to numbers. It’s used with a code book that contains common words longer than about 5 or 6 characters as well as code words. These are then converted to three or four-digit numbers with a prefix of 0 added at the beginning to indicate it is a word from the table.
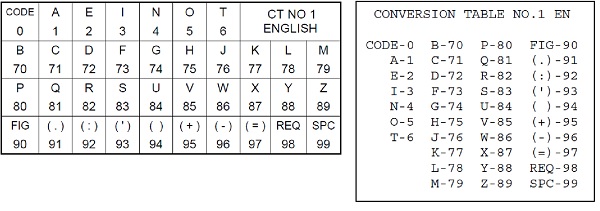
Figure 2 – Character to digits checkerboard with printable version – source:
The Complete Guide to Secure Communications with the One Time Pad Cipher, by Dirk Rijmenants
Alpha characters are assigned digits: 1-6 are used for the most common characters, then double digits starting with 7 or 8 and characters, such as., – +, and space is assigned a two-digit character starting with 9. For example, 99 is a space.
Using numbers has an advantage in that code or commonly used words can be further encrypted by assigning then a number group. Rendezvous can be 2345. Zero can be used as an indicator that the numbers after are a word assignment. This gives 9999 possible commonly used words and code words.
If you make your own checkerboard there is another layer of security. Anyone intercepting the message wouldn’t only need the OTP but the checkerboard AND the code book too.
The process for using and creating your message from an OTP is beyond the scope of this article but I highly recommend The Complete Guide To Secure Communications With The One Time Pad Cipher by Dirk Rijmenants, and Signals Handbook for Small Teams.
One potential problem with any encryption can occur if you have different parties trying to communicate. You must make sure everyone on the net uses the same page at the same time. One way to prevent this is to have one pad for ‘sent’ or ‘outbound’ messages and one for inbound messages. An additional technique is that the first letter group is the pad page number.
However, from a COMSEC standpoint if there is only one set of the pad and one group gets compromised then all messages are compromised. Also, you may not want to send the message to all the groups so having a pad unique to a specific group is a way of adding a layer of security. Although it’s another set of pads you need to create. The golden rule with OTPs is that it’s only used ONCE. It must be destroyed after the message is sent. OTP’s are impossible to break IF you only use it once. Sometimes the radio operator may not be the person encoding or decoding the message, so this adds another layer of security to your messages.
There are a couple of programs that will create OTPs, OTP Generator by Dirk Rijmenants is one. As with the DRYAD sheet generator make sure the key you use to create the OTP is a long string and change it for every pad created. Pads need to be long enough for most messages. I suggest no more than 250 characters otherwise sending your message takes too long. The longer you take to send a message the easier it is for an adversary to find your location. Never send a message from your home base if anyone is trying to find you.
As with all coded messages, code words, and one-time pad ciphers, the code book has to be shared with all parties to start with. Ideally, this should be done face to face because any transmission method to send it presents a COMSEC risk that could be compromised. You should have a send pad and a receive pad so there is no chance of sending using a pad that has already been used. This works especially well when you have multiple groups to send messages.

Transmitting numbers by voice is one way to transmit over the air and you can hear numbers stations on the air even today. Using digital methods can add another layer of security. Morse code is a very good way to transmit messages as the equipment is fairly simple and even a low power 5-watt signal can be heard around the world. Also, the number of people who can read morse code is relatively small. However, in morse code numbers are 5 characters. Another technique is to assign shorter morse characters to each digit. For example, 0 in morse is —– (5 dashes, or ‘dah’s’), by assigning a. (dit) we have shortened the time to send but also added another level of encryption as in normal morse code a ‘dit’ is E.
Regardless of the methods used to pass coded messages, the radio operators must follow good COMSEC procedures. The only way a one-time pad cipher can be broken is if it’s not destroyed after a single us or it’s compromised. A pad can be compromised as easily as not storing securely or not passed to the other operators by a secure method.
Regular participation in scheduled traffic nets done by Amateur Radio operators gives you the skills to copy a message as it is passed. It will also teach you how to pass a message so that others can copy it. As with all skills, you should practice communications skills regularly. Have a small group of people who send and receive at least two or three messages a week is the only way to be proficient with OTPs.
