
Security is always the first job when it comes to defense. The average family may not give it much thought but once someone is trying to harm you or take your stuff, it’s too late to put a plan together. The attacker in most cases has already created a plan and catching you off guard is often a key point in the attack plan. The common sense keys to personal security are know your surroundings, be aware of places where someone could hide until you get close, be in the moment and not distracted. Don’t allow people in your personal space and don’t allow them to lower your guard through deception. Be prepared to react as quickly and decisively as needed. Always have an escape plan.
That is all fine and dandy when you’re walking through a mall parking lot but what about when at your home? Actually, those rules also apply to physical security as well. The good news is that you can easily reinforce your physical security ahead of time. As you prepare your plan, keep in mind that security is always best when it’s planned in layers and based on reality. Your skills, fitness, and tools at hand will guide the response to any threat. Knowing your limitations is important when creating a security plan.

It should go without saying that operational security also applies at the family level. Keeping your business and possessions private will go a long way to keeping you off the radar of criminals. Physical security includes reducing the attractiveness of your home as a target. If it looks like a juicy target from the street or sounds like a big soft target from conversation, you’re already showing weakness.
The flip side of that coin is that if the home looks like a fortress, it can also become a target. Effective security is about finding the sweet spot where people will choose to comply and isn’t too restrictive. First, we need to get some insight into what goes into a security plan and identify some key concepts.
Preparing the Security Plan
A threat is an adversary who is intent on damaging or destroying property and injuring or killing personnel.
A hazard is a physical condition or naturally occurring event that may adversely affect or endanger life, property, or operations.
Both threats and hazards should be carefully considered in the preparation of the security plan. The best way to prepare is to properly perform a hazard analysis as this will identify potential dangers. The analysis is the best way to ensure that all angles are considered and nothing overlooked.
When preparing for the security of a location the plan should be examined for gaps and blind spots but not be so restrictive that it impairs daily operations or becomes too complicated. The primary goal of the security plan is to maintain a sensible and sustainable program to protect the community, the personnel, and the assets that will offer the best chance of success in a crisis environment. A good security plan also makes for a safer environment for all involved. Safety is a critical concept that must not be overlooked or ignored just because of the imagined nature of a survival scenario. In fact, safety becomes a more important concern due to the potential for reduced emergency services and supplies. Also keep in mind the impact to manpower and community morale should tragedy strike. In a potential survival situation, this is especially true if an accident was preventable.
The process to develop a security plan will focus on key elements, including but not limited to: protection, people, operations, intel/information, plus how events inside and outside of your perimeter may affect the situation. When developing a plan, it’s important to understand the interdependence of the people and operations so as to not cause undue hardship or gaps in normal operations.

Continuity of operations should be maintained and any restrictions that are placed should be done in a compartmented way so as to preserve the integrity of any critical processes. For example, don’t place a non-penetrable fortified barrier in the path of water sources and final defensive positions of the home. Should this be the case during a siege for example, it would become overly difficult to secure the water needed for survival if you had to fall back to the final position. If such a blind spot were discovered in an hour of need, the results could be disastrous. If a similar condition cannot be helped it would be wise to form a contingency plan. Contingency plans can be lifesavers if care is taken to create them thoughtfully and practice as needed.
Another point to keep in mind when refining the plan is that security is always a compromise between restriction of operations and resources available. At some point a level of security may not be practical or valued important enough. For this reason, it’s important to perform a hazard analysis and establish priorities. Establishing priorities allows the community to mitigate the hazards deemed most threatening. Once you have determined the threats, vulnerabilities, and assigned ranking priorities, you can now form your strategic plan. This will give you actual tasks to perform to implement your new security plan.

In most cases a security plan is incremental, that is to say you will provide temporary security until permanent measures are in place. An example of incremental implementation would be the Berlin Wall and the rest of the Iron Curtain as it was rolled out in Germany. The wall began as a checkpoint, then a series of checkpoints, then wire barriers were run, then concrete walls and fortifications were constructed. Ultimately there was a network of data connected sectors secured with minefields and tank traps. This continued throughout the Country until Germany was effectively bisected.
Security Planning Methodology
Physical security planning, regardless of whether it’s for the home or a group of structures requires an understanding of the basic elements of security. In the case of potential physical attack it’s helpful to understand the operational acts needed to conduct an attack.
The basic elements of security are:
Deterrence
Deterrence includes physical and psychological barriers to discourage an attack.

Examples include walls, lights, guards, signage, cameras, or even projecting the appearance of a worthless target. Perhaps a place that has already been looted or burned out. The image of a safety or illness hazard can also be a deterrent.
Detection
Detection means to monitor for potential weakness or breaches of the physical property.
Examples include physical patrols, monitored cameras, alarms, sentries, etc.

Delay
Delay means trying to slow intruders down long enough for a response team to arrive or react from within. It also includes preventing intruders from reaching critical assets.
Examples include barriers, tanglefoot wire, water features, access points, chokepoints, creating indecisiveness, breaking the momentum of the attack either physically or psychologically, etc.
Response
Response means actions by humans to engage a security threat before they reach their objective. A Quick Response Force (QRF) is prepared to immediately respond to an incident or breach. In the case of a family in a home, this would mean everyone has a predetermined job to do. These jobs should be planned, communicated, and practiced as needed. This is where the delay part of the plan is critical. Your time to action must be quicker than the time between detection and length of delay you were able to force on the intruders.
Recovery

Recovery is the process to regain normal operations after an event.
Examples include activities such as repair of facilities, reconstitution of personnel and arms, maintenance and positioning of equipment.
Re-evaluation
Re-evaluation is a constant process of plan review. Has there been any change in personnel, goals, threats, or area to be protected? Was your plan effective? What needs to change for the next attack?
(Hint) It’s always wise to change up security, so you don’t become predictable.
All of these basic elements of security are interdependent and must work together in order to create an effective security plan. To bring it down to its most basic level, the four main concepts in security for the small group or home in a survival situation are deter, detect, delay, and defend. These concepts are simple, clear, and easy to remember. At its core, the goal of the community’s security plan is to deter people from targeting the home. If they do decide to target the home, they should be delayed through physical measures long enough for the family to respond and defend the location with tactical advantage.

If there are gaps in the security plan or between the basic elements, the response to an intrusion event will be disjointed or non-existent. For example, installing cameras will be ineffective to initiate a live response if no one is actively monitoring them. If there isn’t a fence of some type to delay an intruder, there may not be enough time to respond before the intruder is on top of you.
Individual Residence Security
Personal living spaces are the final personal defensive position for residents and families in most cases. Personal spaces are also where the family will spend most of their collective time. As such, the living space should be granted a high priority of protection and the least public access. Privacy and personal space are important to morale. Regardless of lodging arrangements it’s important to establish a policy of respect to this end.
Homes and lodging areas should be well considered in the overall protective plan. They should be situated away from perimeter boundaries as much as possible. In cases where this isn’t practical it will be prudent to plan for those residents to fall back to a more protective location. The central fallback location should be of appropriate size and outfitted to accommodate the expected number of people.

The individual residences should have a plan of defense against both intrusion and fire. The exterior of each home should be designed in such a way as to reduce blind spots, protect egress points from intrusion, and channel any foot traffic into outward facing fields of observation, if possible. Opportunities for unobtrusive, defensive property improvements should be explored. These should include but not be limited to: durable planters, columns, landscape wall benches, timber features, etc. The improvements should be aesthetic in nature but have the ability to prevent penetration by a fired projectile. They should also provide visual concealment or ballistic protection for a resident while under retreat into the safety of the home. The same features should reduce the cover and concealment options of an intruder approaching from beyond the property. Installing area denial materials and defensive landscaping street side of any such feature will accomplish this.
An effective method of evaluating your home as a visual target is to identify blind spots and channels by placing yourself as the intruder. Survey the approaches to your property from every exterior angle and from a distance. If anything in the yard can be used as concealment as you approach, that’s a blind spot you should address. Either remove it or use some form of area denial feature. If you want an intruder to arrive at a specific spot, create channels to put him there. Use anything that would be difficult to move through. This includes tactical landscaping, water features, barriers, debris, and anything on the ground that would impede progress. For example, people will usually walk around cactus gardens and deep water.

It’s recommended that each home install a fence constructed of chain link or wood panel to reduce avenues of approach and aid in channeling. Wood fences should be solid panel and reinforced to reduce the vulnerability of breaching by adding an additional horizontal board near the lower one-third of each panel section. Entry gates should have two firm latching and locking mechanisms to prevent unauthorized entry. Each latch should be located directly across from the upper and lower hinge assembly. Hinge assemblies should be configured to prevent the lifting of the gate off the hinges.
Chain link fencing should be no less than four feet in height. Plants of an entangling nature or with protective thorns or needles should be located directly adjacent to all fence sections not located in direct street side field of view. Such landscape will deter entry to the property by climbing or breaching the fence. Entry gates should be positioned in a location easily observed from within the home. Hinges on gates should be positioned in opposite facing directions to prevent the gate from being lifted off the hinge and removed. Latches should be installed snugly and, in a fashion, to reduce failure from kicking of the gate. A locking feature should be added. Heavy duty cable locks can be added to both the latch and hinge sides of any gate to prevent removal or opening of it if the hinges are unbolted.
Large tree branches should be pruned away from all fences and structures to prevent an intruder from using it as a ladder to gain entry over the fence or onto/into the structure. This will also aid in the fire defense plan, which calls for all flammable vegetation to be cleared as far as possible from the home. This includes trees that may provide the ladder effect for flames to top trees and spread to rooftops.

If the home is yet to be built, there are some design concepts that would support the security plan. Residences should consider the building materials of the home during the design phase. There is a tradeoff between protection, energy requirements, cost of construction, and fire resistance. For example, a home constructed of wood siding will offer less ballistic and fire protection than a CMU/CBS structure. A tilt wall construction will offer better protection overall. An asphalt shingle roof may be less expensive than cement tile but has a shorter lifespan and less fire protection. Egress points must also be considered when designing the resistant home. Ballistic windows are preferred if one is concerned about projectiles but they can be very expensive. Hurricane rated windows are next best. For further savings and good protection, standard windows with quality shutters will be sufficient.
Security film on windows should be avoided unless it’s factory installed and extends into the window frame all the way to the edge of the glass. If film is added after the windows are installed a solid strike will cause the entire window to fail and collapse from the window frame. For ease and quickness, a roll-down shutter design is recommended. Heavy material drapes should be incorporated into the design to act as blackout curtains in hours of darkness and to prevent observation of activities from outside the residence.

The structure entry doors should be solid core, hurricane rated, or commercial quality wood or steel. There should be no glass panels or glass sidelights or windows within arm’s reach of the doorknob or deadbolt. The frame should be ballistic/kinetic impact resistant and mounted securely with minimum 6” Tapcon type screws on 6” centers driven into the structural framing. This is to reduce failure in case of weather or intruder. Exterior doors should open outward and the hinges should be of anti-intrusion design. The door should include a wide-angle fisheye style peep sight to see a wide area of the front porch. A quality deadbolt should be installed with a burglar plate covering the latches. The deadbolt shouldn’t use a key from the inside unless it’s kept near the door in case of fire evacuation.
As a second option to reduce failure or kinetic intrusion, a heavy-duty net can be placed behind doors or windows. It’s easily applied and removed by installing heavy eye hooks around and into the frame. The eye hooks can be concealed by curtains and such for aesthetic reasons. In the absence of a net, heavy duty cordage can be laced on the hooks in a way to catch the door should it be forced from the hinges. Such a method will disrupt the attacker’s momentum allowing the residents to escape, evade, or secure defensive positions within the home.

For a final stand style of defense, interior channeling of intruders can be created to draw them into desirable routes and destinations within the home. Tactical placement of furniture and household items along with hiding, camouflaging, or structurally narrowing interior doorways can confuse and delay intruders.
Ideally all utilities will be buried from the utility pole to the home. Casings should be placed over any communication wires to prevent landlines and alarm wires from being cut. Electrical panels should be secured with a padlock to prevent tampering.

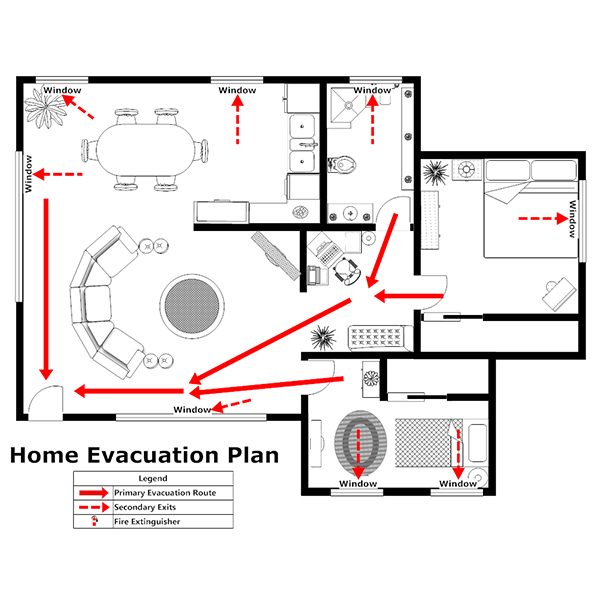
Each home should have a fire evacuation plan and an appropriate number of fire extinguishers thoughtfully located in the home. Each family should identify a meeting place in case of separation. The community should identify a gathering location for each planned phase of development. There should also be a central community gathering location for residents to fall back to for protection and information. This evacuation/meeting plan must be communicated to all family members and practiced.
Each home should have some form of communication with each family member and preferably with someone who can assist in times of emergency. It’s also recommended that each home utilize a NOAA Weather Radio with SAME technology for local emergency broadcast information.

Each home should have at least two planned avenues of escape to opposite directions of the property. Escape routes should lead toward a pre-planned rally point and be easily recognizable to residents in darkness as well as light. In case of evacuation it will be important to have any keys necessary to pass through yard gates as well as negotiating any defensive measures located on the property. Again, everyone in the family must be aware of this.
You are in charge of security and your family is depending on you whether they know it or not. Take some common sense approaches to reducing your home as a target. If all else fails, be able to work together safely to defend it.
Plan now, be ready later.
