Home Cybersecurity
BLUF: While we do not personally have control over widespread cyberattacks, there are basic steps we can take at home to avoid breeches, malware, and PII disclosure.
 》Encrypt sensitive files.
》Encrypt sensitive files.
》Use end-to-end encrypted messaging apps for sensitive conversations or file shares. (Signal app)
》Backup data routinely to an offline hard drive.
》Keep operating systems up-to-date. Opt for auto updates.
》Follow best practices for passwords, use acronyms to make a complex password that can still be remembered. Enable two step authentication.
》Don’t click on unknown origin links. Don’t open suspicious emails.
》Use virus, spyware, adware, and firewall protections.
》Use a VPN for anonymity and secure on the web.
》Keep social posts private, don’t use your real name.
Quick Change
BLUF: The ability to quickly change your appearance can aid in surveillance operations and counter-surveillance scenarios where you’re the target.
 Wear clothing with dual appearance features such as a reversible jacket or beanie that’s a different color on the inside.
Wear clothing with dual appearance features such as a reversible jacket or beanie that’s a different color on the inside.
Wear or carry easily removable clothing and accessories that can be removed or worn while on the move. A ball cap can be flipped backwards or stuff in your pocket. Glasses can be stowed quickly or a worn poncho can be discarded.
Adjust gait, stance, and mannerisms. A quick change in how you carry yourself can alter your appearance to others. If you are observed on one occasion taking short strides and keeping your head down, as you move out of the field of view of your observer/target, begin taking longer steps with your head held high.
》Remember the 51% rule. Dress/act like the majority of those around you. If more than half are wearing business casual, then swim trunks or a tuxedo would make you standout.
How to PIT a Vehicle.
BLUF: A Precision Immobilization Technique (PIT) is a maneuver that may temporarily immobilize a vehicle allowing you to egress and engage.
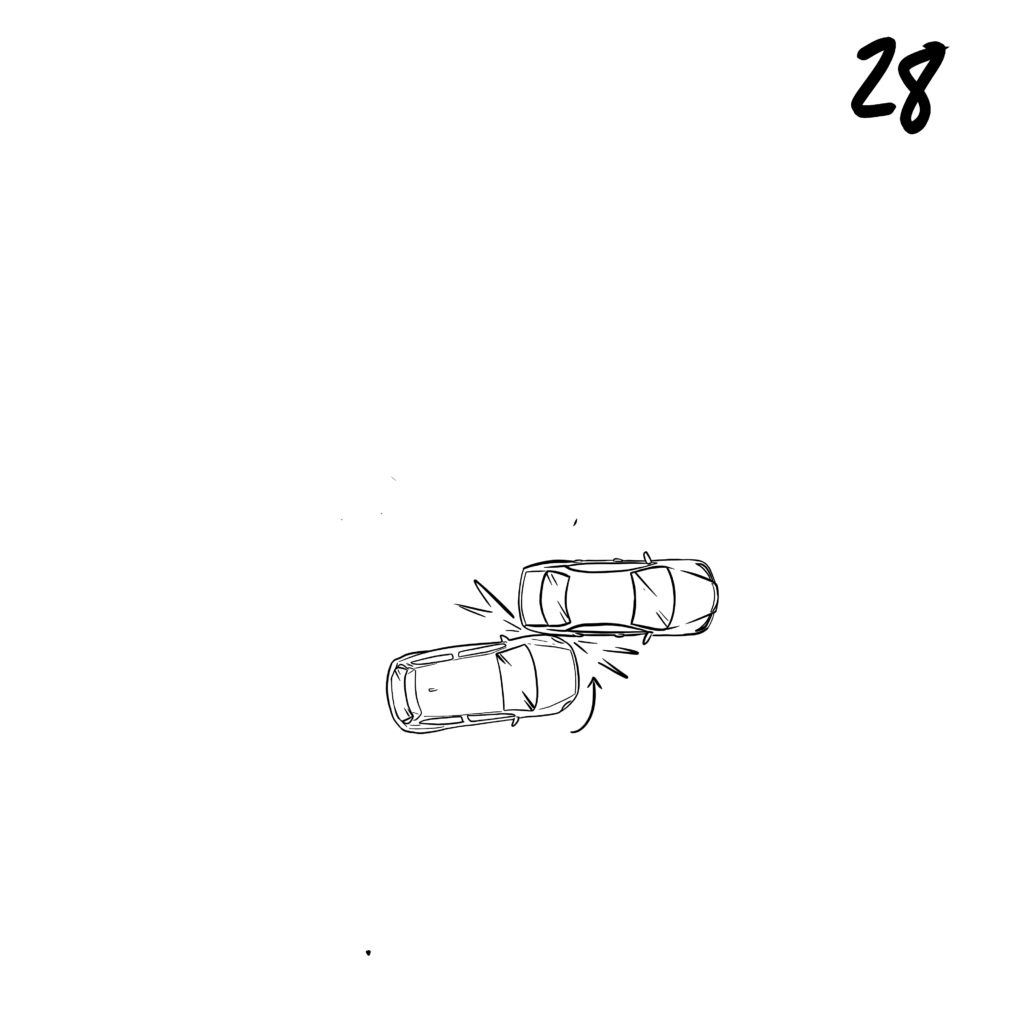 》Begin to overtake target vehicle until your front bumper is online with their rear tire well. Match target’s speed.
》Begin to overtake target vehicle until your front bumper is online with their rear tire well. Match target’s speed.
》Turn into the target’s rear and maintain speed or accelerate as needed to match target’s speed until target loses traction. You are not making a 90° turn, it’s more comparative to a commitment lane change.
》After contact, push through target and accelerate away from the direction of their spin.
If the safety of the target vehicle is of concern, do not PIT at speeds greater than 45 (sedan) or 35 (SUV/truck). A successful PIT will only momentarily disable for seconds.
Learn more about Vehicle Safety, Security, and Bugging out here.
Everyday Carry
BLUF: Carrying essentials on your person can aid in daily tasks or survival.
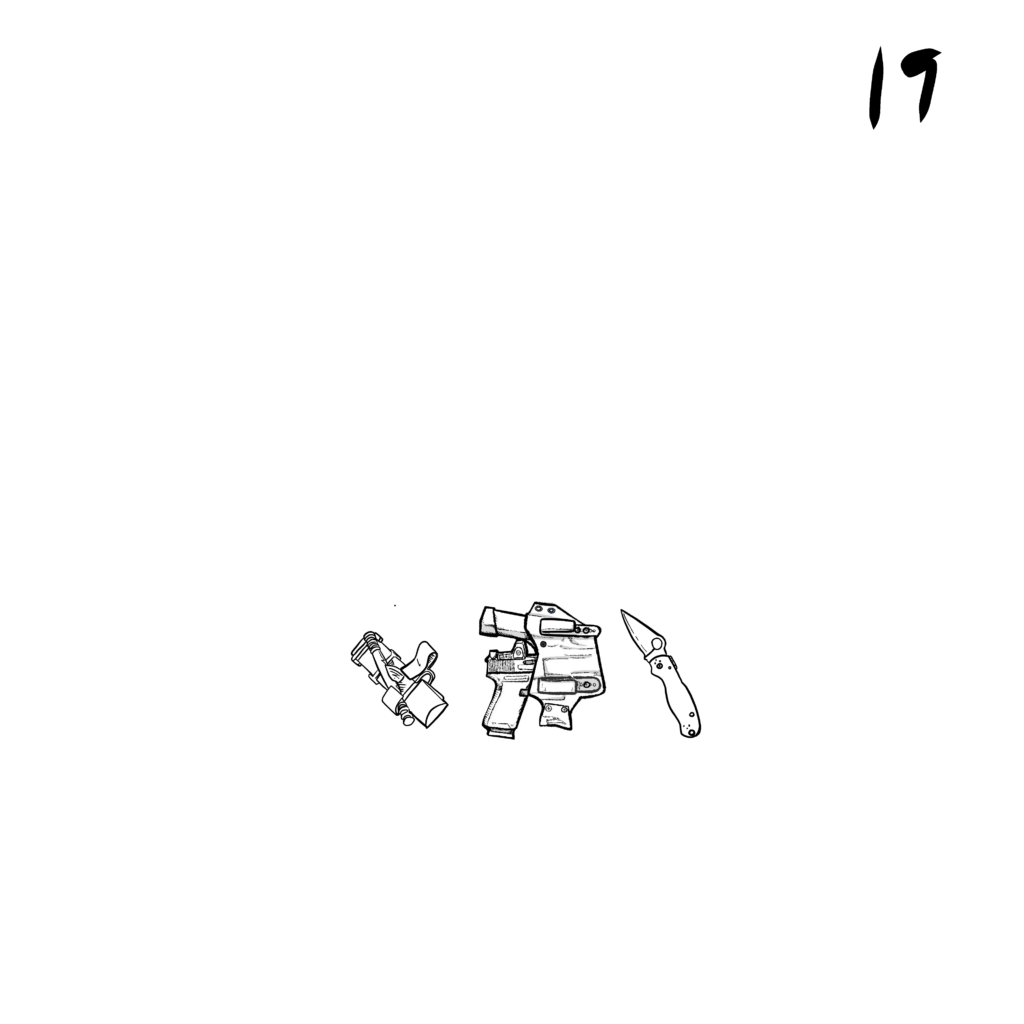 Baseline Carry: Basic supplies for daily tasks.
Baseline Carry: Basic supplies for daily tasks.
》Basics – Wallet/Purse, Cash/Credit/ID, Keys, Phone
》Supplies – Pen/Pencil/Marker, Paper/Notepad
》Wear – Sunglasses, Hat, Watch, Handkerchief
》Tools – Multitool, Lighter, Knife, Flashlight
Prepared Carry: Circumstantial equipment for heightened threats.
》Defense – Handgun (concealed), spare mag/s
》Medical – Tourniquet, IFAK, N95
》Survival – Handcuff Key, Whistle, Compass, Map, PSK (Personal Survival Kit)
While this is a lengthy list, if carefully selected and positioned about your person, most items can go unnoticed and will not be cumbersome.
Get the Grayman EDC Guide here.
Password Selection
BLUF: It’s difficult to create a password complex enough to offer protection yet simple enough to remember. There’s a workaround.
 Combining several types of characters is an extremely effective way to make your password more cryptic. Use a mix of lowercase and uppercase letters, numbers, and symbols. You’ll also need to use 11 characters or more. It would take 400 years to crack a code using that formula.
Combining several types of characters is an extremely effective way to make your password more cryptic. Use a mix of lowercase and uppercase letters, numbers, and symbols. You’ll also need to use 11 characters or more. It would take 400 years to crack a code using that formula.
However, it can be a difficult to remember a code of that complexity, much less all your various passwords. Try one of these techniques below,
》Rebus- a riddle or puzzle made up of letters, pictures, or symbols whose names sound like the parts or syllables of a word or phrase.
Example: NE1410S? 》Anyone for Tennis?
》Leetspeak- a method of typing words using alternate characters. Letters are replaced with numbers or symbols that closely resemble them.
Example: @ny0nefort€nn!$? Anyone for Tennis?
》Acronyms- a replacement of words for the their first letter.
Example- AOFT? or AFT? 》Anyone for Tennis?
You don’t want all your passwords to be the same for every account. While your new code may be near unhackable; it can be compromised by over-the-shoulder surveillance, key loggers, and breaches. Consider a simple preparatory word for each type of account. For example, for all your banks use Bank@ny0nefort€nn!$? for Gmail and Protonmail use Email@ny0nefort€nn!$?. You get the idea, put your own spin on it.
P.S. Turn on 2 Factor Authentication that uses your phone and not just an email. Make sure your phone has a screen lock too.
HIP POCKET BRIEF
Lessons on Tactics, Techniques, and Procedures (TTPs)
A Hip Pocket Brief is an informal, short, and concise training session. We think these briefs will be helpful to add some extra tactics to your “toolkit”. Below are three of our recent off the hip sessions posted unredacted at bit.ly/TheGBC and summarized on our free Telegram channel at t.me/graymanbriefing
